
Cybersecurity Basics for Small Businesses (Part 1)
Traditionally, many small businesses have not seen the need for investing in cybersecurity. This usually comes down to the assumption that they are simply not going to be targeted when much larger businesses exist. It’s only natural to assume that the bigger the prey, the larger the target is on their back. However, in today’s world, the truth of the matter is that cyber criminals target small businesses for exactly this reason. They are expecting small businesses to have their guard down. Because of this, every small business needs to invest in basic security prevention measures to ensure they are not seen as “low hanging fruit”.
In this article, we will provide you some easy–to–implement security tips that you can use right away!
1. TURN ON MFA (Multi-Factor Authentication) FOR EVERYTHING
If there’s one thing modern, digital security can’t go without these days, it’s Multi-Factor Authentication (MFA). If you don’t know, MFA is an authentication system in which a user must present “two or more pieces of evidence” to gain access to something. These pieces of evidence can be anything from a password, secret personal question, a security token, fingerprint ID, or more.
This method’s multiple layers of security instantly make it harder for hackers to attack your business, blocking “over 99.9 percent of account compromise attacks”. To give an example, if a cybercriminal manages to steal a password of yours, they’ll still need at least one more form of authentication to access the account.
Thankfully, most applications offer some form of MFA these days. This also means, however, that if you’re using an app that doesn’t offer MFA, you should think twice about its safety and whether you should be using the app at all (you probably shouldn’t).
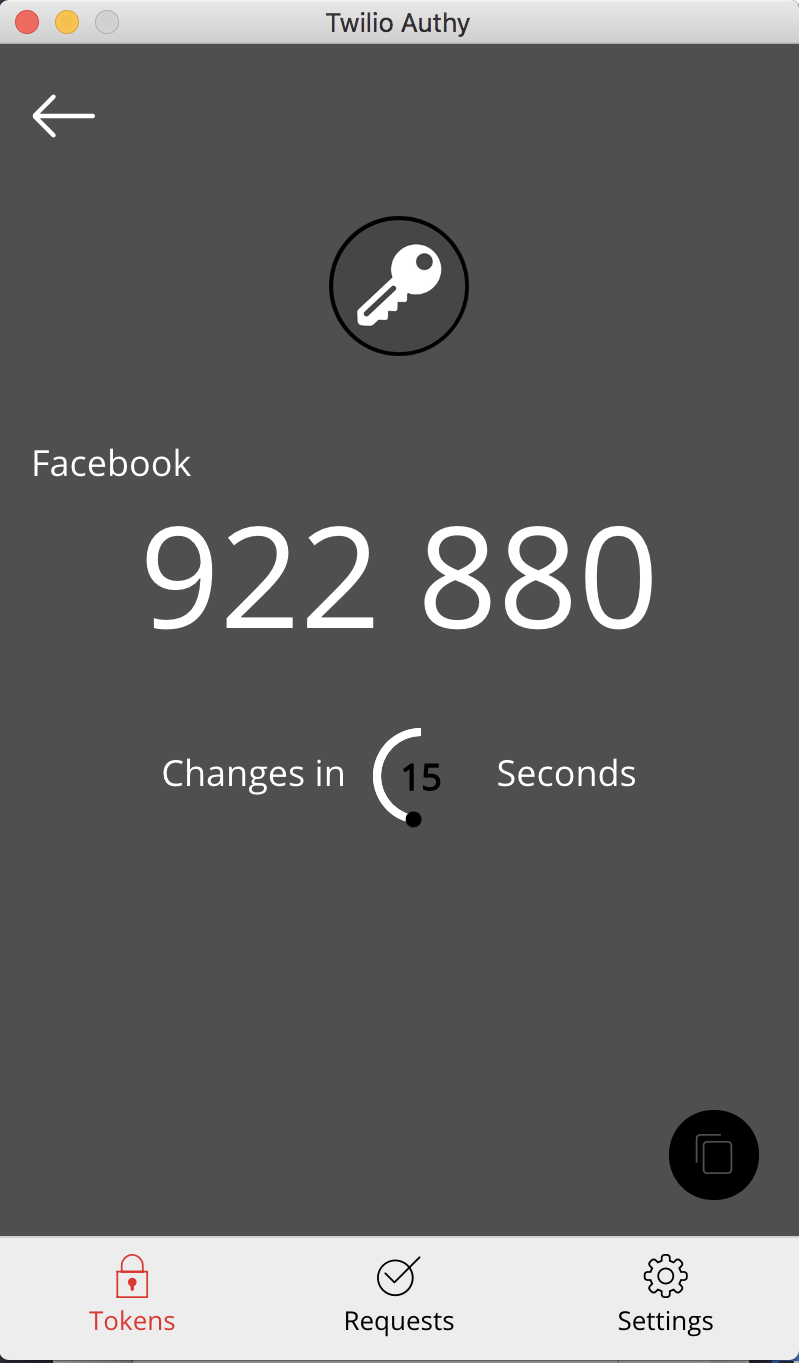 Knowing this, it’s important to get your hands on an authenticator app such as Microsoft Authenticator or Google Authenticator. These apps are free and work well, but their one downside is that they require you to pull out your phone anytime you need to enter the 2FA (Two-Factor Authentication) code. If you find this an issue and want to streamline the process, then Authy is also an app worth considering. While you can still download Authy to your mobile, it also gives the option of using a PC/Mac version of the application. This means you can conveniently copy the code straight from your desktop, without needing to pull out your phone which can act as a distraction in the workplace.
Knowing this, it’s important to get your hands on an authenticator app such as Microsoft Authenticator or Google Authenticator. These apps are free and work well, but their one downside is that they require you to pull out your phone anytime you need to enter the 2FA (Two-Factor Authentication) code. If you find this an issue and want to streamline the process, then Authy is also an app worth considering. While you can still download Authy to your mobile, it also gives the option of using a PC/Mac version of the application. This means you can conveniently copy the code straight from your desktop, without needing to pull out your phone which can act as a distraction in the workplace.
(Image on the left: Authy’s desktop 2FA system – reloading you a new code every 30 seconds)
In addition, Authy allows you to easily move your MFA codes across to new devices (e.g. when acquiring a new phone/laptop) without having to set them up again, which can often take hours if you have many accounts to move. This is something many people don’t even consider until it‘s too late.
A bonus tip: Never use SMS (text messaging service) for your MFA (or anything fragile for that matter) as it can be easily intercepted.
If you’re interested in learning more about MFA, check out our other article focusing on its benefits towards security.
2. NEVER SHARE PASSWORDS OR LOGINS
Continuing on from our bonus tip, an unfortunate common practice in many businesses is to share login details among staff. This is not a good idea. When doing this, it immediately spreads the responsibility of keeping information secure across multiple people. Most people leave MFA off when sharing passwords, and who knows how careful they are with their own data in general? And what’s worse is when one of these people leaves your organisation. In our experience, passwords are rarely changed, which often means that even ex-employees still have access to login.

As stated on Security Boulevard, “72% of individuals reuse passwords in their personal life while nearly half (49%) of employees simply change or add a digit or character to their password when updating their company password every 90 days.“
This lack of caution many people have in regards to their passwords simply makes sharing them more harmful than beneficial. However, if you’re in a position where you absolutely need to share your password, it’s important to use a secure transferring method such as Onetimesecret, which we discuss in detail on our blog here. Secondly, it’s also worthwhile setting yourself a reminder to change your shared details not long after having done so, resolving any doubts that your data is at future risk.
3. BE WARY OF CHANGING BANK DETAILS
An all too common and dangerous scam used by hackers these days is to send an invoice which appears to come from an existing client/partner/vendor with updated bank details. Too many times this results in the transfer of large sums of money to the hacker’s bank account and, in many cases, this is irreversible and not covered by most cyber insurance policies.
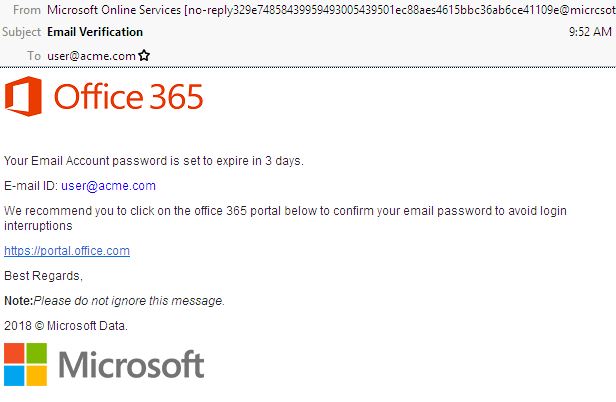
(Below: An example of a scam bank email which sends you to a fake Microsoft login page)
(Below: An example of a falsified invoice email)
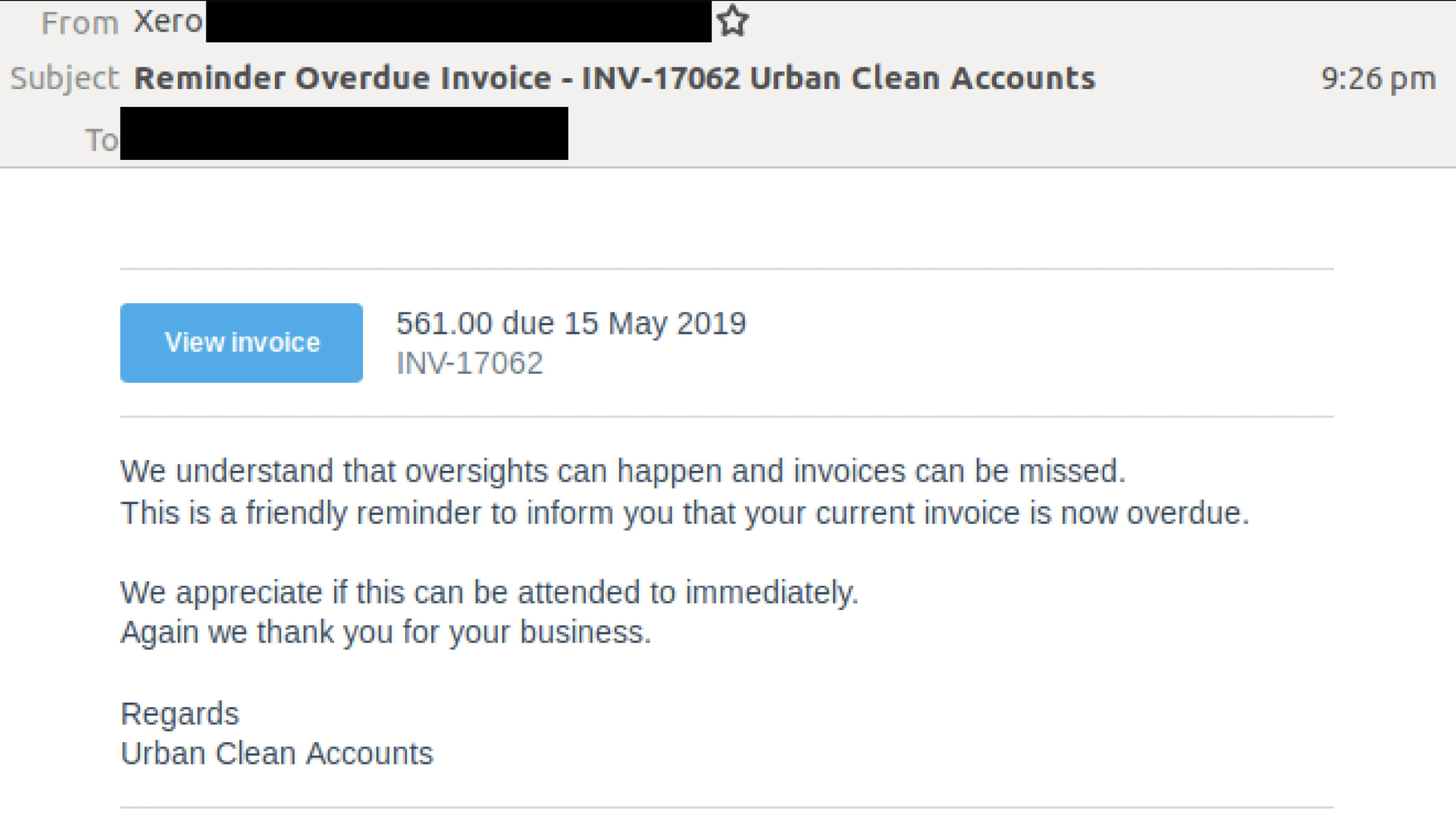
To avoid this trap in the future, enact a policy which requires authorisation from a second employee in your organisation before changing any bank details. In addition, make sure you contact the issuer of the invoice to confirm the contents of the email. And, whatever you do, make sure to lookup their phone number and do not use the phone number on the invoice. The scammers are expecting that you may try to contact them, so they will have changed the phone number and contact details within the invoice/email.
4. MANAGE THE RISK OF PHISHING EMAILS
As you can see in the example images above, phishing emails can be very sophisticated and hard to spot. They are easily the most popular and successful form of online scam committed by criminals, often sent out to thousands of people at a time. The way in which they mimic organisations and individuals you think you know are exactly how they trick so many into handing over personal information and large sums of money.
Some warning signs to look out for when receiving these emails/messages are if they’re claiming there’s an issue with your account/payment details, that they’ve noticed suspicious log-in attempts, they ask you to confirm personal information, they ask you to click on a link to make a payment, they offer you free money, etc.
If you do receive something like this and have doubts, it’s also wise to check with someone you trust. At Axiom IT, we offer a free service to our clients that enables them to forward us any suspicious emails that will be vetted by our helpdesk whenever they have any doubts. Thus, it’s equally imperative to have your own business team trained and ready for when they receive these suspicious messages, so they know to send these suspicious emails to whichever IT company you are partnered with, whether it’s us or someone else.
SECURING THE FUTURE
To recap, in order to begin keeping your business in a safe and prepared position from here on out, make sure to utilise Multi-Factor Authentication, cease sharing login details with others, be wary of phishing emails, and be prepared to ask for help when unsure. Axiom IT proudly offers help and training to our clients in all of these areas, keeping them secure against any of these breaches. For more information, call us at 1300 991 992 or email [email protected]. You can also visit our contact page for more information.